VMProtect CRC Handling (CRC Checks) Part 1
Hello Friends,
Today I am gonna share a trick for bypassing the CRC checks of VMProtect. VMProtect is using a hash system to verify the checksum of file. Here I have a file protected by VMProtect. I patched a byte and now It is showing a Message Box.This is the MessageBox that will appear if we modify the Original file. Our goal is bypass the check and make the file working.
For bypassing CRC checks. Firstly we gonna set a HWBP on execution on api CreateFileW and then HWBP on CreateFileMappingW and then MapViewOfFile. Our last bp is MapViewOfFile.
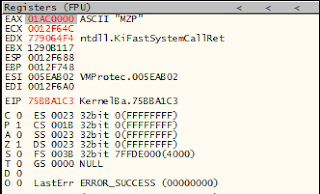
Once the last HWBP executed clear all the Breakpoints and press CTRL+F4 and we will reached at the end of the function. Now we can see that the EAX holds the VA of our file. In my case VA is 01AC0000
Now lets find the VA 01AC0000 in memory and set memory breakpoint on access and execute the target.
After execution we reached at
00630A5E 3202 XOR AL,BYTE PTR DS:[EDX] ; crc function break
Lets investigate this function. Press F7 and see whats happening. I analysed the function and found some values.
0062FB53 D0ED SHR CH,1 ; loop start
0062FB55 89C1 MOV ECX,EAX
0062FB57 51 PUSH ECX
0062FB58 60 PUSHAD
0062FB59 E8 3D150000 CALL VMProtec.0063109B
0063109B C1E0 07 SHL EAX,0x7
0063109E 66:0FA3DB BT BX,BX
006310A2 9C PUSHFD
006310A3 C1E9 19 SHR ECX,0x19
006310A6 F9 STC
006310A7 ^E9 AAF9FFFF JMP VMProtec.00630A56
00630A56 F9 STC
00630A57 09C8 OR EAX,ECX
00630A59 F9 STC
00630A5A 0FBAE5 15 BT EBP,0x15
00630A5E 3202 XOR AL,BYTE PTR DS:[EDX] ; crc function break
00630A60 ^E9 ACE3FFFF JMP VMProtec.0062EE11
0062EE11 66:C74424 08 030>MOV WORD PTR SS:[ESP+0x8],0x503
0062EE18 42 INC EDX
0062EE19 68 D7988109 PUSH 0x98198D7
0062EE1E 891C24 MOV DWORD PTR SS:[ESP],EBX
0062EE21 68 E8F9D11A PUSH 0x1AD1F9E8
0062EE26 E9 3F1F0000 JMP VMProtec.00630D6A
00630D6A FF4D 00 DEC DWORD PTR SS:[EBP] ; length of bytes
00630D6D 53 PUSH EBX
00630D6E E8 52DDFFFF CALL VMProtec.0062EAC5
0062EAC5 8D6424 3C LEA ESP,DWORD PTR SS:[ESP+0x3C]
0062EAC9 0F85 84100000 JNZ VMProtec.0062FB53 ; loop jump
0062EACF 68 6D5A4433 PUSH 0x33445A6D
0062EAD4 8945 00 MOV DWORD PTR SS:[EBP],EAX ; final hash
0062EAD7 51 PUSH ECX
0062EAD8 9C PUSHFD
0062EAD9 60 PUSHAD
0062EADA 8D6424 2C LEA ESP,DWORD PTR SS:[ESP+0x2C]
After some analysis I found that there is a loop function which is creating a hash for a fixed size of bytes. I posted the whole function above. I removed the mem bp and put a soft bp at VA 0062EAD4 because this is the first write after loop. Now run the target. EAX holds a hash in my case hash is 99FE991A
Now I decided to compare the hash with original file. So I fire up olly and load the Original target and do the same procedure above after stop at VA 0062EAD4 I saw that EAX holds different hash. Now copy the eax and put it at our target and try to run. Bingo! the file run without any error. It means we need to write an inline patch for bypassing it purely. We will do it in next part.
Hopefully this will helps for bypassing VMP CRC.
PS : My English is not so good but I think people can understand my feelings. :D. If you have any questions regarding this please let me know.
VMProtect CRC Handling (CRC Checks) Part 1
 Reviewed by Amado Best
on
December 03, 2020
Rating:
Reviewed by Amado Best
on
December 03, 2020
Rating:
 Reviewed by Amado Best
on
December 03, 2020
Rating:
Reviewed by Amado Best
on
December 03, 2020
Rating:













![Enigma HWID Patcher Loader Generator [Updated]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhzZ_yZUS0YnBNCXTlzSx9t7jWNkD60pOKwpLZRZet5ZZ78LQXoig08rkZ0RHdGPGyhp9a5KsvDmOhbR7CETDE-BfKQ-K9Oz7D_oTT-QM1u4XxOtG62ugbMpSBqYb-ysxsXKkbQGJPcGmNP/s72-c/Capture.PNG)



No comments:
Post a Comment